HashiCorp Vault is a secure tool designed for accessing confidential information, known as secrets. These secrets encompass sensitive data types, such as API keys, passwords, certificates, etc. Vault offers a unified interface and ensures meticulous access control while maintaining a comprehensive audit log.
Access to diverse secrets like database credentials, API keys, and credentials for service-oriented architecture communication is essential in a modern system. Managing and monitoring access to these secrets can be complex and platform-specific. Vault addresses this challenge by providing a solution incorporating crucial rolling, secure storage, and detailed audit logs.
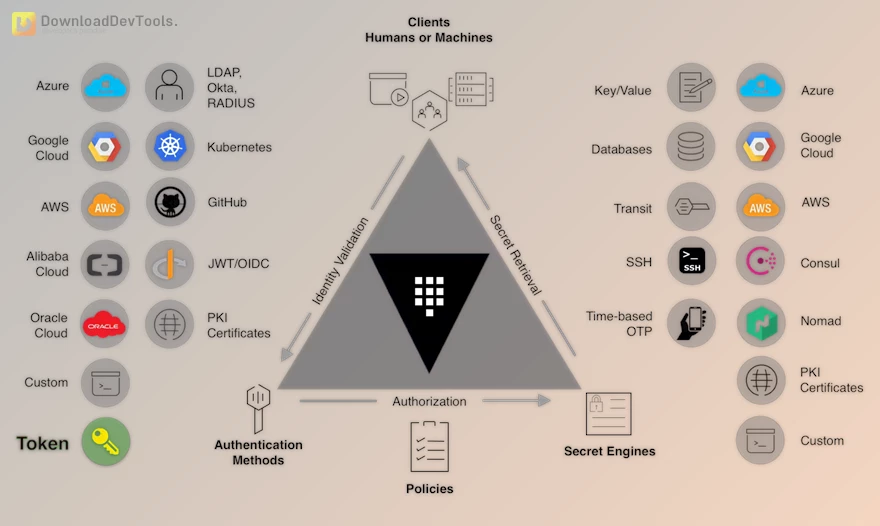
HashiCorp Vault operates as a comprehensive tool for secrets management, encryption as a service, and privileged access management. It seamlessly integrates with trusted identities, automating access to secrets, data, and systems.
Identity-based security is a core feature of Vault, allowing organizations to authenticate and authorize access to secrets and sensitive data automatically.
Vault offers a robust platform for the secure management of secrets and the protection of sensitive data. It enables organizations to securely store and tightly control access to tokens, passwords, certificates, and encryption keys through a user-friendly UI, CLI, or HTTP API.
Key Features of HashiCorp Vault:
- Secure Secret Storage: Vault securely stores arbitrary key/value secrets by encrypting them before writing to persistent storage. Raw storage access alone is insufficient to retrieve secrets. Storage options include disk, Consul, and more.
- Dynamic Secrets: Vault generates on-demand secrets for specific systems like AWS or SQL databases. For instance, when an application requires access to an S3 bucket, it requests credentials from Vault, which dynamically generates AWS key pairs with valid permissions. Vault automatically revokes these dynamic secrets upon lease expiration.
- Data Encryption: Vault performs data encryption and decryption without persistent storage. Security teams can set encryption parameters, enabling developers to store encrypted data in locations like SQL databases without implementing custom encryption methods.
- Leasing and Renewal: All secrets in Vault are associated with a lease. At the lease's end, Vault automatically revokes the associated secret. Clients can renew leases using built-in renew APIs.
- Revocation: Vault incorporates built-in support for secret revocation. It can revoke not only individual secrets but also entire trees of secrets. For example, revoking all secrets read by a specific user or all secrets of a particular type. This feature aids in essential rolling and securing systems during an intrusion.
Click on the links below to Download the latest version of HashiCorp Vault with Keygen!

 HashiCorp Vault v1.21.3 Enterprise Edition for Win x86 + Keygen.rar (Size: 168.5 MB - Date: 2/16/2026 10:44:00 AM)
HashiCorp Vault v1.21.3 Enterprise Edition for Win x86 + Keygen.rar (Size: 168.5 MB - Date: 2/16/2026 10:44:00 AM) HashiCorp Vault v1.21.3 Enterprise Edition for Win x64 + Keygen.rar (Size: 178.1 MB - Date: 2/16/2026 10:43:58 AM)
HashiCorp Vault v1.21.3 Enterprise Edition for Win x64 + Keygen.rar (Size: 178.1 MB - Date: 2/16/2026 10:43:58 AM) HashiCorp Vault v1.17.3 Enterprise Edition for macOS x64 + Keygen.rar (Size: 168.5 MB - Date: 11/28/2025 6:21:15 PM)
HashiCorp Vault v1.17.3 Enterprise Edition for macOS x64 + Keygen.rar (Size: 168.5 MB - Date: 11/28/2025 6:21:15 PM)
















